Table of Content
- Remote Desktop (RDP) Hacking 101: I can see your desktop from here!
- How to Remotely Access Another Computer Over the Internet
- Was this article helpful?
- ) Connection to the Remote Desktop Server from Windows-7 to Windows 10 Home!
- Tech Updates
- Enable Remote Desktop on Windows-10 Home, how to?
- Microsoft Remote Desktop App
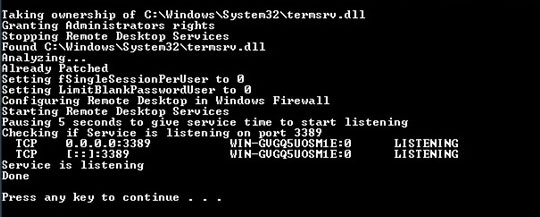
It will continue to send packets until the target machine is unable to handle those packets. It can be observed from the image below that that target machine crashed resulting in a BSOD or Blue Screen of Death. Sorry there is no options for edit, maybe because I’m not a registered user. I have patched it on this version without issues… I even used the AutoPatcher with the following pattern. I think the easiest way for you is to deploy a clean VM with an evaluation version of Windows Server 2016 Essentials and try to edit the termsrv.dll.
The currently supported Windows 10 termsrv.dll version. Concurrent Remote Desktop allows you to simultaneously use a client computer while a standard user is still interactively using it. Imagine never having to kick a person off of their computer because you need to work on it. Concurrent Remote Desktop makes this possible.
Remote Desktop (RDP) Hacking 101: I can see your desktop from here!
Speaking of protection, aside from not using easily guessed usernames, a strong password would also go a long ways toward protecting the account. If hackers can programmatically “guess” your password because it’s based on a simple word – they will quite quickly. On the other hand, if it’s complex, meaning a combination of upper and lower case letters, numbers, and symbols , their task becomes much more daunting. We see that from the victim’s perspective, they open up the Remote Desktop Connection dialogue and try to connect to the machine and user of their choice. It asks for the credentials to connect as any original security authentication prompt.

After 11 months of using the “Remote Desktop Connection” feature, a recent security update left this feature blocked with a prompt to upgrade to Windows Pro for a cool $99. Before we move forward, you must understand that Windows has a Remote Desktop Server and a Remote Desktop Client. Remote Desktop Client is still present in the Home edition, which you can open using the MSTSC cmdlet. This means you can still connect to other devices from a PC with Windows Home. However, the Remote Desktop Server has been removed, which means other devices cannot connect to your Windows Home computer.
How to Remotely Access Another Computer Over the Internet
However, inside the Remote Tab, we see that there is a section labeled as Remote Desktop. This section can be used to Enable or Disable the Remote Desktop Service. For the time being, we are enabling the Service as shown in the image below. Resul is a error after entering of correct password and no options for login “The object invoked has disconnected from it’s clients.”. Had trouble finding the Hex for windows build so i couldn’t patch.
Inside the Account Policies, there exists an Account Lockout Policy. It contains 3 policies each working on an aspect of the Account Lockout. The first one controls the duration of the lockout. This is the time that is required to be passed to log in again after the lockout. This controls the number of invalid attempts.
Was this article helpful?
This will not affect your production environment. Make sure you are searching for a hex value, not text-string, integer, etc. In the HxD hex editor, you have to select the data type and text-string is the default. This solution runs without additional software RDP Wrapper or RD Plus. For this version what code should be looked up for and replaced with. It works but if I try to log in from another PC, in the same account I log off the account of the PC I connect to.
We are looking for a low-cost but sure way to control versioning amongst our developer team. Since Sticky Keys can be initiated by pressing the Shift key 5 times, we connect to the target machine using RDP and then proceed to do so. This will open an elevated command prompt window as shown in the image below. The Bruteforce attack that we just performed can be mitigated. It requires the creation of an Account Policy that will prevent Hydra or any other tool from trying multiple credentials.
There is a long list of tools that can be used to perform a Bruteforce attack but one of the most reliable tools that can make the job done is Hydra. Although called a Bruteforce, it is more like a dictionary attack. We need to make two dictionaries one with a list of probable usernames and another with a list of probable passwords. The dictionaries are named user.txt and pass.txt. We see that a set of credentials was recovered.

In the image below, we have the meterpreter of the machine that has RDP disabled. We use the getgui command on meterpreter to create a user by the name of ignite with a password as 123. After completion, we can log in on the machine as ignite user through RDP. As we enabled a lockout policy, we will not be able to log in on the machine even with the correct password until the time passed that we toggled in the policy. You will be greeted with a Lockout message as shown in the image below. In a network environment, it is a best practice to disable the services that are not being used as they can be the potential cause for a compromise.
I did patch the file as you described and am facing an “interesting” behaviour now. If I log into the machine locally and open a program, this program is not visible in the RDP session. The processes of the programs I opened however are still running . I’m trying to set up an AWS Lightsail instance and ran into a surprising trap. This instance is running Windows Server 2019 and the greedy SOB’s only allow 2 simultaneous RDP connections.
If they can pair that valid User with an easy-to-guess password, they’ve got the keys to your computer’s crown jewels. Although it has been years since its introduction, the Metasploit Framework is still one of the most reliable ways to perform post-exploitation. During Penetration Testing, if there exists a machine that has RDP disabled, it is possible to enable RDP on that device through a meterpreter.
Some other methods and tools can be used to perform this kind of attack but the SETH toolkit is the one that seems elegant. We start with cloning it directly from its GitHub Repository and then installing some pre-requirements. Since we now know that the target is vulnerable, we can move on to exploiting the target. After selecting the exploit, we provide the remote IP address of the machine with the particular target. It can vary based on the Operating System; for Windows 7 use the target as 5.